Every device connected to the internet can become a threat.
This happened to Ellen and Nathan Rigney from Texas who had their WiFi camera network hacked.
The hacker initially sent vulgar voice messages to their baby, then switched cameras to watch Ellen and Nathan, then the hacker threatened to kidnap their baby.
After that incident, Ellen and Nathan threw their cameras away and reported the incident to the police.
Incidents like these can cause psychological scars to individuals and financial damage to enterprises.
In fact, a threat like this would happen much more frequently in the future given the proliferation of IoT devices in homes, businesses, and industries.
Statista reports that IoT total annual revenue worldwide will grow from $181.5 billion in 2020 to $621.6 billion in 2030.
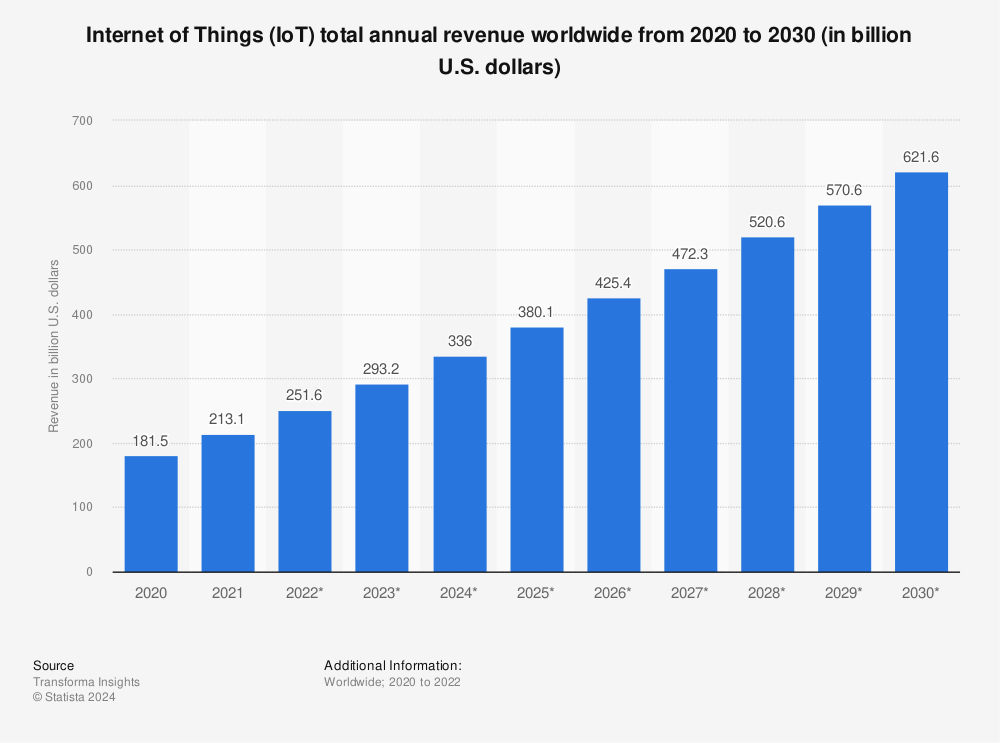
Find more statistics at Statista
Even at home, our next purchase could end up being a “smart” device. Think about how TVs these days are connected to the internet. Or fridges. Or a thermostat.
It’s therefore important to take steps to secure our IoT system, no matter how small it is.
Where do potential vulnerabilities lie in an IoT system?
The parts that make up an IoT system can be broken down into three parts:
- The edge client (your cameras, sensors)
- The gateway which collects and processes your data before sending it somewhere
- The cloud service
- User error, negligence or ignorance
A system is only as strong as its weakest link, which unfortunately means that a weakness in one of your elements could result in a network breach.
IoT gateway security is critical
For most commercial and industrial users of IoT devices, an IoT gateway is at the center of the IoT system.
Hence, this makes IoT gateways an especially vulnerable target for hackers because of its importance within the IoT system.
Why use an IoT gateway?
As IoT systems get more elaborate, it becomes more financially and logistically sound to use an IoT gateway to become the hub for all edge IoT devices to connect to.
For example, if you have just one edge device that transmits data using mobile phone networks, then it doesn’t make sense to have a gateway.
However, if you have 10 such devices, each with its own mobile network connection, it might end up being more financially sound to have a central hub which connects to the internet. This device, known as an IoT gateway, would usually take up the responsibilities of processing data and sending it to the cloud.
Since these functions are transferred to the gateway, the edge client can be much more optimized – for example, by using a cheaper, less powerful processor since it doesn’t need to process data anymore.
It would also not need to have cellular networking hardware anymore. Instead, it will now connect to the IoT gateway using a more efficient, lower cost and better optimized networking protocol.
Why is an IoT gateway a potential digital security risk?
The previous example showed how an IoT system went from:
Edge device -> Cloud
With the addition of the IoT gateway, this is the data transmission path:
Edge device -> IoT gateway -> Cloud
This results in an extra element in the IoT system that can be vulnerable to attacks.
Furthermore, IoT gateways are likely the most powerful device in the system.
As they are now tasked with data transmission and processing, IoT gateways therefore need a host of hardware that is up to the task.
Compared to an edge device, an IoT gateway will likely have more processing power, more RAM, more software (and an operating system) and more network connections.
A typical IoT gateway will likely have a gigahertz of processing power and a gigabyte of RAM, compared to individual devices and sensors which can have very low-powered microcontrollers with processing power measured in megahertz and RAM measured in megabytes, if not kilobytes.
The following table will show the main points of differentiation between an IoT gateway and edge clients.
| IoT gateway | Edge client | |
| Processing power | Equivalent to a low-powered personal computer | Very low powered |
| RAM | At least 1GB | MB or KB |
| Operating system | Yes, likely Linux | No, usually a microcontroller |
| Software | Yes | Generally no software beyond the program to fulfill the edge client’s function |
| Networks | WiFi, 433MHz, LTE, LoRa, BLE, ZigBee | Usually only one network |
| Power | Usually always on | Might be in sleep mode |
As you notice in the table, keeping an IoT gateway secure is serious business because with power comes responsibility.
A bad actor could penetrate into the gateway, whether physically, using malware or exploiting a vulnerability in software, networking or hardware.
How to secure your IoT devices
Securing an IoT device requires a regular and thorough checkup of your system’s security as every system has its own vulnerabilities and weaknesses.
Nonetheless, here are some simple guidelines that can ensure greater security today.
Regular updates of software and components
One of the best ways to keep yourself secure when it comes to hardware and software involves keeping them up to date.
Manufacturers sometimes find weaknesses in the hardware’s firmware and release firmware updates. Often, keeping these updated is as simple as clicking a button when you see the notification on the front-end.
Software is similar. If your gateway has an operating system, make sure to keep it updated. If it has any software, make sure to update those also.
Turning on auto-updates will help you keep your software up to date with no extra work needed on your part.
Insecure data protections
Wireless data transmission is similar to shouting in public. Anyone who speaks your language will be able to understand it.
Stored data and data that’s being transmitted should be secured using cryptographic algorithms. If you have any expectation of privacy, it’s important that you avoid insecure, unencrypted transmission of data.
Oftentimes, buying low-quality products will cause these problems. There are IP cameras out there sending surveillance footage over HTTP. Hackers have found these cameras and posted them online for the whole world to see.
It’s therefore important to buy IoT products that are designed with privacy and security in mind.
Easily breakable cryptography and passwords
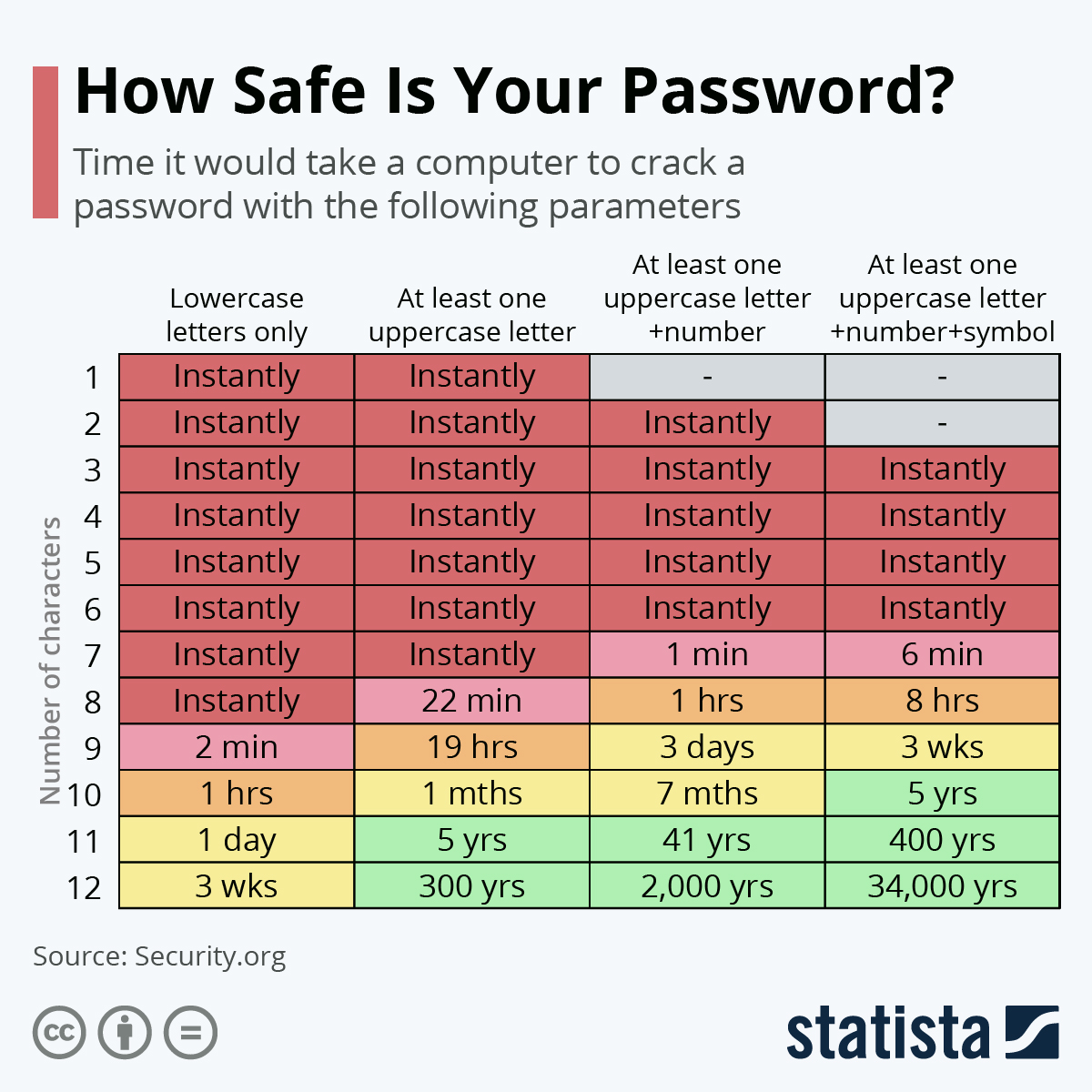
You will find more infographics at Statista
As computers get more powerful, outdated cryptography has become easily crackable.
Similarly, password strength has to keep up with new computers’ ability to brute force passwords.
As you can see from the table by Statista above, a strong password is long, mixed cases have numbers and symbols making cracking a password very difficult.
While it’s a rookie mistake, it’s worth pointing out that the first thing everyone should do when they buy a new device is to change all the passwords.
Most new devices will make you declare a new password upon logging in for the first time. However, if they don’t, your goal is to ensure that the admin dashboard login and/or the device login password are completely different from what is printed in the manual or sticker on the device.
Wireless network broadcasting too widely
Protecting an IoT network means keeping entry points to a minimum, on a need-to-enter basis.
A lot of devices will be configured to ensure that the majority of the use cases are covered.
Furthermore, device manufacturers generally will shy away from suppressing the broadcast power because it will affect the user’s experience.
Nonetheless, one thing that you can do is to ensure that you tune the broadcasting power of your router, gateway, and devices to as low as necessary.
This ensures that neighbors don’t get an easy way to enter your networks. For example, if your WiFi network can be reached by a neighbor, you are more or less granting unlimited opportunities to break into your network.
In this case, it’s also best to shut off public broadcasting of SSIDs.
Separate networks for IoT and business/home
It can be tempting to run your IoT devices and business or home network on the same device but it’s generally advisable to separate them.
This ensures that a weak link in your network does not compromise your business or personal data.
Avoid mixing IoT components
One of the best things you can do for security is to buy your components from a single manufacturer.
Different IoT device manufacturers would design their data management systems and protocols a bit differently.
Although there’s always a way to get some interoperability between these devices, it becomes inefficient when your devices cross brand boundaries. For example, in order to ensure greater compatibility, a device might be sending a much larger payload with excessive information across.
Or you might be forced to use a different networking protocol just to communicate with a device.
In order to manage these differences between devices, compromises have to be made. Unfortunately, each compromise can also potentially create gaps in security.
Dusun makes a comprehensive list of IoT products for home, business, and industrial use with a focus on streamlining security and interoperability.
Designing a secure system
Since the IoT gateway and cloud are two areas that have the most control over your IoT system, it’s important to have a system set up to ensure that your system can notify and manage anything that is out of the ordinary.
Iot gateway cloud and gateway software security
Before any threats can happen, you can start by creating rules around who can access your device and what kind of permissions they have.
For starters, it’s important to ensure your passwords are complex and that you have multi-factor authentication set up if possible.
Then, ensure that you configure your access controls. Ensure that people who only need to see the data on it do not have admin access. Ensure that people only see the data that they need for them to operate.
In addition, ensure there are rate limits in your system. Ensuring that people cannot brute force their way into the system is important. Do this by ensuring that people who try to brute force a password can only do so a limited amount of times before they are locked out for a period of time.
Plus, you should establish baselines and use machine learning techniques to automate threat detection. With baseline data, you will know that if there’s a big spike in activity, that could mean that there is an attack going on.
Finally, set up IP filtering so that access to your IoT cloud service and IoT gateway can only be accessed through specific devices and ban everything else. Of course, it’s important to ensure that the secure devices’ IP addresses don’t change or else you could inadvertently lock yourself out.
IoT gateway hardware security
At home, we probably leave our routers out in the open.
However, when it comes to IoT gateway security, it’s important to ensure that these rooms are kept physically inaccessible to most people except a select few.
Physical access to an IoT gateway can cause significant problems because a bad actor can install sniffers and interceptors via USB or ethernet connections.
It’s therefore important to first ensure that these devices are locked up in a difficult-to-access area. It’s also advisable to disable any unnecessary physical ports on the gateway – USB is probably the easiest target to start with.
Establish the IoT gateway’s identity
In order to avoid a man-in-the-middle attack, it’s important to set up a system that isn’t susceptible to such attacks.
To start, you must establish a reliable identity for your gateway device by giving it a digital certificate.
Dusun’s IoT products support SSL/TLS certificates to ensure that data is kept safe from prying eyes and sniffers.
The use of SSL certificates ensures that data is sent over secure connections between elements in an IoT system. This helps you ensure that data isn’t being leaked out inadvertently and ensures the security of your data for privacy regulations compliance.
To go a step further, you could use hardware to store your private keys. In order to ensure that the private keys cannot be cloned, you will need to embed a Trusted Platform Module into your gateway via a Physical Unclonable Function. These are the hardware that is embedded on a device to ensure that only that specific gateway has the private keys.
With the gateway now secured, you could consider going a step further and securing your edge devices.
Threat modeling and regular reviews
Finally, let’s talk about how you can build resilience into a system.
At the start of every IoT system’s build, one must consider the threat vectors that you might be facing based on your physical circumstances and human factors.
For example, is your network susceptible to neighbors or visitors attacking it? Are new employees trained for security purposes? Are the new devices a threat? Do people who have elevated access still require those credentials?
Circumstances change over time as the organization grows, which is why it’s important to schedule a regular meeting to review how these circumstances have changed.
Conclusion
Tackling security risks is very important to keep data private, and ensure the security of your home or business.
Crime, sabotage, and invasions of privacy can scar people psychologically and cost a lot of financial damage to enterprises.
This article talked about the ways you can beef up your IoT gateway security and how to strengthen the links between it, the cloud and edge clients.
IoT security is an ongoing process. You have to set it up to be as strong as possible by default and then periodically review it to ensure an updated security plan.
One of the best things you can do for yourself is to look for a manufacturer that has the sensors, edge clients, and gateways that fit your use case.
Dusun is a specialist IoT provider who has products for home, business, and industry. Since we are an end-to-end producer of IoT products, we are able to create a cohesive and secure IoT system that minimizes risk from mix-and-match IoT systems.
Further Reading