As the number of IoT devices continues to increase, the total amount of IoT devices in the world has surpassed non-IoT devices. And by 2030, 75% of all devices are forecast to be IoT. Communication or connectivity between IoT devices has become an important topic at present. To make your IoT device connected to the Internet easily , there are several IoT protocols available with different performance, data rate, coverage, power and memory, and each protocol has its own advantages and or more or less disadvantages.
The key aspect of choosing a perfect IoT wireless protocol for your IoT project is to pen down your requirements clearly so that you can focus only on viable options. These requirements can be the data transmission rate, operational range, power consumption, and the cost of the whole project.
Wireless communication devices realize data communication between devices or with serial servers under various IoT protocols. And many different types of IoT wireless protocol has already been widely used in Internet of Things hardware devices and machine-to-machine (M2M) communication.
IEEE has more than ten 802.15 technical task groups right now(https://en.wikipedia.org/wiki/IEEE_802.15). These 802.15 task groups include: WPAN/Bluetooth, Coexistence, high-rate WPAN, low-rate WPAN, mesh network, body area network and visible light communication, and so on. Each of these wireless transmission protocols has different performance, communication rate, coverage, power and memory. Next, Dusun IoT will share with you the commonly seen IoT wireless protocols.
What Is IoT Technology (Internet of Things)
Before talking with IoT protocols, we suggested you can make a basic understanding of IoT firstly. The Internet of Things (IoT) is a broader term for the ever-increasing number of smart devices that can send or receive data over the internet.
Let us ask a question. Did you ever think you would be able to talk to your refrigerator? It certainly didn’t a decade ago. But the Internet of Things, or IoT, makes otherwise “dumb” refrigerator “smarter” by giving it the ability to “listen” to you while communicating over the internet through wired or wireless technologies.
Smart Home IoT
The IoT revolutionizes the universe of physical objects by imparting data processing, advanced analytics, and internet connectivity. The concept of a “smart home” is the epitome of the IoT and its application at a personal level. Using a mobile app or a website, you can adjust the thermostat temperature, turn on/off the lights, check the state of smoke detectors, unlock the doors, and even ring the doorbell because all of them are connected to a central IoT hub where data is communicated over the internet.
Learn about Smart Homes Here:
Industrial Internet of Things
In terms of Industrial Internet of Things (IIoT), IIoT works wonders by embedding billions of internet-enabled sensors and devices, emanating streams of data analyzed using AI (Artificial Intelligence) algorithms to improve operational efficiencies in manufacturing and distribution systems. This data enables analysts to predict potential machine breakdowns, optimize performance parameters, and prevent resource underutilization.
Learn more about the IIoT Here:
What is IoT Protocol and Why is It Necessary?
Wireless protocol allows the devices to communicate without wires and cables over long distances. Since the dawn of the twenty-first century, IoT wireless communication has made possible the establishment of a vast, intricately interconnected network with over 20 billion devices throughout the world. These devices can sense, process, transmit, and receive data over a network spanning millions of miles. These devices encompass various industrial sectors ranging from oil & gas, manufacturing, production, and service-based organizations such as banks, telecommunications, and hospitality, etc.
Notwithstanding, a secure connection is a must-have for these devices to communicate. And this constitutes the basis for IoT protocol development.
IoT Wireless Protocol Pros and Cons
Pros:
- No need for hefty physical infrastructures like wires, cables, and antennas.
- Wireless networks are relatively easy to install and cost-effective to maintain and supervise.
- Data is transmitted or received instantaneously.
- Relatively easy to detect faults and perform diagnostics as compared to wired networks.
- Wireless networks allow users more mobility as the network can be easily mobilized and reinstalled.
Cons
- As communication happens in open spaces, wireless technologies are deemed less secure.
- They are relatively more susceptible to signal interference and hence, are more unreliable.
- Data throughput can be affected in extreme weather conditions like storms etc.
- Data speeds vary depending on the distance to the network.
- Wireless technologies have a limited range.
Different Types of IoT Procotols
We generally divide the IoT protocols into two categories, one is is typically in charge of networking and communication between devices in the subnet, and the other is primarily a device communication protocol that runs on the conventional Internet TCP/IP protocol, is in charge of data exchange and communication between devices over the Internet. To let me better understand its difference, we would like to make a concept clear: Open Systems Interconnection (OSI) model.
What is OSI model?
Computer network system that offers various services and functions are quite sophisticated. As a result, the OSI model was created to increase the popularity of network applications. It aims to recommend all businesses to use this specification to manage the network, so that all companies can be connected by having the same specification. ISO model divides the entire communication function into seven layers according to those principles:
- All nodes in the network have the same layers;
- Different nodes perform the same functions at the equal layer;
- Adjacent layers within the same node communicate through interfaces;
- Each layer utilizes the services offered by the lower layer and renders services to its upper layer;
- peer layers of different nodes carry out peer-to-peer layer communication in accordance with the protocol.
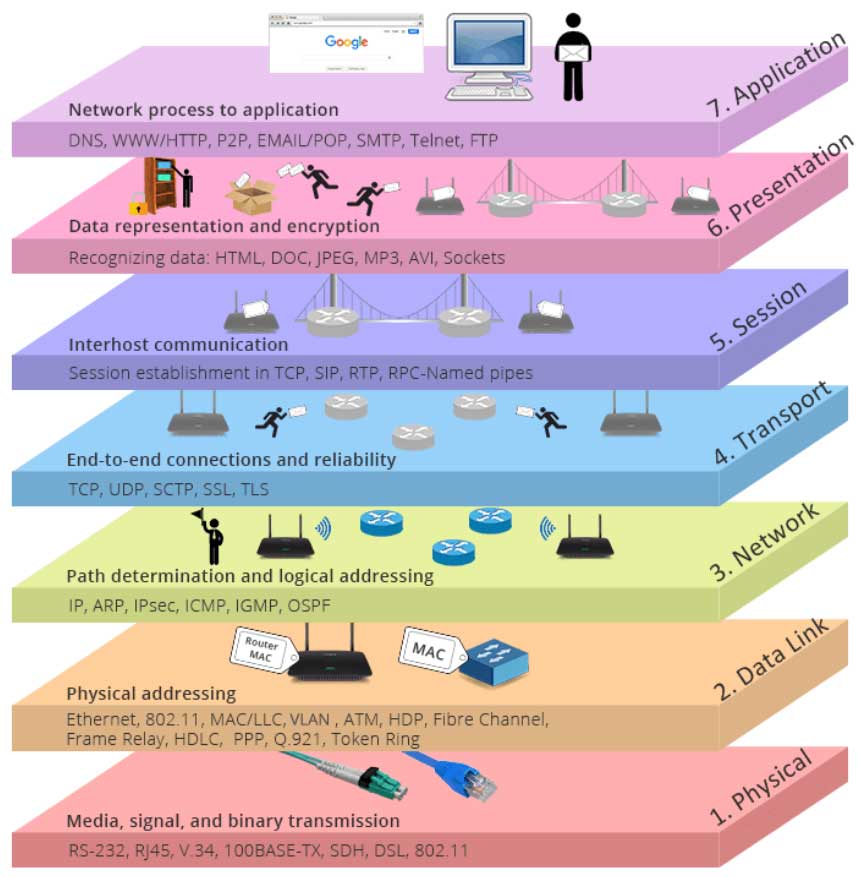
Application Layer
The application layer refers to the application that communicates with other computers, and it mainly corresponds to the communication service of the application program.
For instance, a word processing programme that do not have communication function is not able to execute code that communicates, and the programmer working on this programme may not care about OSI layer 7 at all. However, if it is necessary to add a a file transfer option, this word processing programme must support OSI layer 7. Examples include SMTP, NFS, TELNET, HTTP, and FTP.
Presentation Layer
Data format and encryption definition are the primary responsibilities of the presentation layer.
For instance, FTP gives you the option to send data in binary or ASCII format. If binary is chosen, neither the sender nor the receiver can alter the file’s contents. If the ASCII format is chosen, the sender will convert the text from the sender’s character set to standard ASCII and then send the data. And the receiving side convert standard ASCII to the character set of the receiving computer.
Session Layer
The session layer specifies how to start, control and end a session. This process include the control and management of multiple bidirectional messages, so that the application layer can be notified when only a portion of a continuous message is complete. This will make the data seen by the presentation layer is continuous. The presentation layer may occasionally be represented by the data if it has received all the data. For instance, RPC, SQL, etc.
Transport Layer
The capabilities of the transport layer include three aspects:
- choosing between error recovery protocol and an error-free recovery protocols;
- multiplex the input of data streams of various applications on the same host;
- Reorder received data packets that are not in the correct order.
Examples include: TCP, UDP, SPX.
Network Layer
The network layer defines the end-to-end packet transmission. It specifies the logical address that may identify every node, as well as the way of routing implementation and learning. The network layer also defines how to divide a packet into smaller packets in order to adapt to the transmission medium whose maximum transmission unit length is less than the packet length. Examples include IP, IPX, etc.
Data Link Layer
The data link layer establishes the parameters for data transmission across a single link. These protocols are related to the various media being discussed. Examples include ATM, FDDI, etc.
Physical Layer
Physical layer is about the properties of the transmission media and the specification usually refer to the standards developed by other organizations. Connectors, frames, use of frames, current, coding, and light modulation are all part of the various physical layer specifications. To define all the details, the physical layer also frequently employs numerous specifications. Examples include Rj45, 802.3, etc.
IoT Protocol Overview
In IoT applications, communication technologies include Wi-Fi, RFID, NFC, ZigBee, Bluetooth, LoRa, NB-IoT, GSM, GPRS, 3/4/5G networks, Ethernet, RS232, RS485, USB, etc. And related communication protocols (protocol stacks, technical standards) include Wi-Fi (IEEE 802.11b), RFID, NFC, ZigBee, Bluetooth, LoRa, NB-IoT, CDMA/TDMA, TCP/IP, WCDMA, TD-SCDMA, TD -LTE, FDD-LTE, TCP/IP, HTTP, etc. The communication protocols used in the technical IoT framework system mainly include: AMQP, JMS, REST, HTTP/HTTPS, COAP, DDS, MQTT, etc.
The communication environment of the IoT includes Ethernet, Wi-Fi, RFID, NFC (Near Field Communication), Zigbee, 6LoWPAN (IPV6 over Low-speed Wireless Personal Area Networks), Bluetooth, GSM, GPRS, GPS, 3G, 4G, etc., and each has a certain scope of application. For instance, AMQP, JMS, and REST/HTTP all work on Ethernet. The COAP protocol is specially developed for resource-constrained devices, while DDS and MQTT are much more compatible.
In general, we classify the IoT communication protocols into four groups: short-range communication, long-distance cellular communication, long-distance non-cellular communication, and wired communication. And let’s dive deeper into the realm of these IoT protocols and try to fathom their functions and applications.
Short Range Protocols in IoT
RFID
Radio Frequency Identification (RFID) is a kind of automatic identification technology. It employs radio frequency to execute non-contact two-way data transfer and to read recording media (electronic tags or radio frequency cards), so as to identify targets and exchange data. According to how the tags are powered, RFID technology can be categorized into three groups: passive RFID, active RFID, and semi-active RFID.
Passive RFID
Passive RFID is the one that debuted first, is the most developed, and has the widest use among them all. By accepting the microwave signal transmitted by the radio frequency identification reader and obtaining energy through the electromagnetic induction coil to supply itself for a short time, a passive RFID electronic tag can complete the information exchange.
Because the power supply system is omitted, the size of passive RFID products can reach centimeter-level or even smaller, and have features of simple structure, low cost, low failure rate, and long service life. But as a price, the effective identification distance of passive RFID is usually short, and it is generally used for short-distance contact identification. Passive RFID mainly operates in the lower frequency bands of 125KHz, 13.56MKHz, etc., and its typical applications include: bus cards, ID cards, canteen meal cards, etc.
Active RFID
The rise of active RFID is not long, but it has played an indispensable role in various fields, most notably the expressway’s electronic non-stop toll collection system. Active RFID items are usually powered by an external power source and actively sends signals to RFID readers. Their volume are relatively large, but they also have a longer transmission distance and a higher transmission speed. A typical active RFID tag can make contact with an RFID reader at a distance of 100 meters, and the read rate can reach 1,700 read/sec.
Active RFID operates mostly in higher frequency bands such as 900MHz, 2.45GHz, and 5.8GHz, and is able to identifying multiple tags simultaneously. Active RFID is indispensable in various radio frequency identification applications that demand higher performance and a large range due to its features of wide range and high efficiency.
Semi-active RFID
Semi-active RFID is a compromise for passive RFID and active RFID, and it is also called low-frequency activation trigger technology. Semi-active RFID products are typically in a dormant state and only supply power to the portion that retains data, so their power consumption is low and can last for a long time. When the tag enters the RFID reader’s identification range, the reader will activates it by using low-frequency signals first and then using high-frequency signals to quickly transmit data. Its typical application situation is to activate semi-active RFID items across an expansive area covered by a high-frequency signal. Numerous low-frequency readers are positioned at various points to completes location as well as information gathering and transmission.
NFC
NFC is the abbreviation of Near Field Communication. It is a short-range high-frequency wireless communication technology that enables point-to-point data transmission between electronic devices without physical touch (within 10 cm). Consumers may exchange information and access content and services easily and intuitively thanks to NFC’s simple and touch-based solution. This technology evolved from contactless RFID and is backward compatible with RFID. It was first promoted by Philips, Nokia and Sony, and may be mainly used in handheld devices such as mobile phones.
Benefits of Using NFC
NFC is regarded to have tremendous application prospects in industries like mobile payment because of its near-field security. It combines peer-to-peer, contactless card reader, and card functionality into a single chip, creating a plethora of new lifestyle possibilities for users. In contrast to RFID, NFC uses two-way identification and connectivity. It works in 13.56MHz frequency range within a 20cm radius, and is able to quickly and automatically establish a wireless network, providing the connection for Bluetooth, Wi-Fi, and cellular devices, allowing electronic devices to communicate over a short distance.
NFC Application Scenarios
NFC Payment
NFC payment primarily refers to an open-loop application that transforms a mobile phone with NFC functionality into a bank card to use in supermarkets and shopping malls.
NFC Security
NFC security is mostly used to transform the mobile phone into a virtual access control card and save the data from an existing access control card in the NFC of the mobile phone. In this way, there is not need to carry extra access control card.
NFC Tags
Writing some information onto an NFC tag allows users to instantly access the it by just waving the NFC tag in front of an NFC-enabled phone. For instance, retailers can attach NFC tags to storefront doors that hold posters, flyers, and promotions. Consumers can use NFC mobile phones to obtain relevant information according to their own needs.
Bluetooth
Bluetooth technology was named after a 10th-century Danish king, “Herald Blatand” where “Blatand” means “Bluetooth”. It aims to bring a short-range and low-cost wireless communication technology relying on radio frequency waves in the 2.45 GHz spectrum and allows two devices to communicate with each other for quick data transfers.
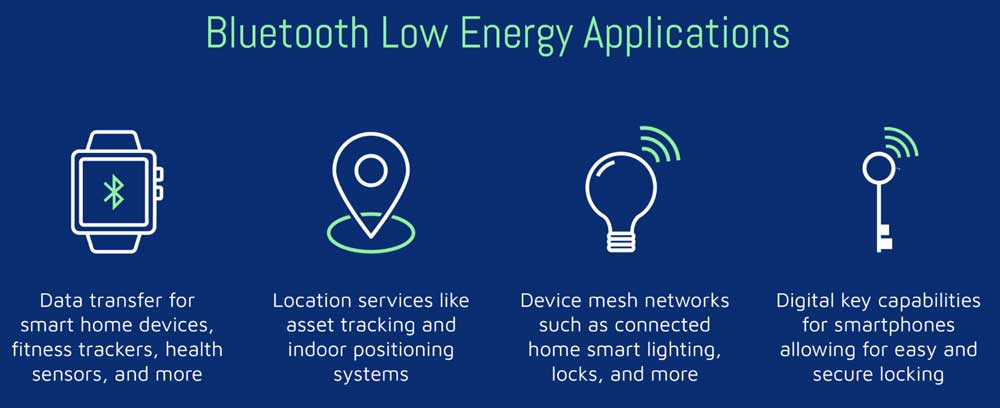
Bluetoooth Features
Bluetooth transmission has three different distance levels, with Class 1 being around 100 meters, Class 2 being approximately 10 meters, and Class 3 being approximately 2-3 meters. Its normal operating range is a 10-meter radius, under normal conditions. Within this range, interconnection between multiple devices is possible. Meanwhile, Bluetooth-enabled devices use the “Frequency Hopping Spread Spectrum” technique, which makes them much more secure and prevents hackers from eavesdropping.
Bluetooth is now managed by the Bluetooth Special Interest Group (SIG), and is used for exchanging data between fixed and mobile devices over short distances and building personal area networks (PANs). A Bluetooth device manufacturer must meet Bluetooth SIG standards to market it.
Bluetooth Low Energy (BLE) is designed to provide considerably reduced power consumption and cost while maintaining a similar communication range. It is mainly used at novel IoT applications in the healthcare, fitness, beacons, security, and home entertainment industries. It is independent of classic Bluetooth and has no compatibility.
Read further: Bluetooth versions
Bluetooth Pairing
To make sure that the data sent by one Bluetooth device will only be acknowledged by the other device with authorization, two Bluetooth devices must be paired before they make connection. Bluetooth technology divides devices into two types: master and slave.
Typically, a Bluetooth master has an input. Master devices include Bluetooth mobile phones, Bluetooth-enabled PCs, and Bluetooth gateways. generally do not have an input. So, when the slave device leaves the factory, a 4-digit or 6-digit matching password is solidified in its Bluetooth chip. Slave devices include UD digital pens, Bluetooth headsets, and more. The slave device cannot be matched with the slave device, however the master device and the master device as well as the master device and the slave device can. Additionally, a master device may be associated with one or more other devices.
Bluetooth Uses
Today, a myriad of PEDs (Personal Electronic Devices) employs Bluetooth technology. For example, wearable devices like headphones, air pods, or devices like wireless keyboards, mice, printers, webcams, etc. With the popularity of Bluetooth IoT, Bluetooth technology also been widely used in fitness bracelets, smart watches or remote patient monitoring wearables to make RPM IoT solutions. Also, By integrating AoA locator and indoor positioning system together, Bluetooth is also widely used for personnel and asset location tracking.
Z-Wave
Z-Wave was introduced by Zensys, a Denmark-based company, in 1999. By creating a mesh network using low-power RF waves operating in the sub-1 GHz band, Z-Wave has revolutionized the world of residential and commercial building automation.
Z-wave is somewhat similar to Wi-Fi, which has been fine-tuned for smart home automation. The Z-Wave Alliance is an international conglomerate of more than 300 companies that are currently managing this technology. These companies have manufactured and introduced an astonishing number of more than 100 million smart devices working on Z-Wave.
These devices include but are not limited to various smart home devices like door locks, thermostats, lights, sensors, fan controllers, and security systems. You can use your smartphone, laptop, or tablet to control and monitor a Z-Wave system remotely or even locally, through a dedicated smart panel with a Z-Wave gateway serving as the central hub and controller.
The typical range for Z-Wave varies from 100-800 meters, while for Z-Wave LR, the range extends up to 1,600 meters.
Wi-Fi
The Wi-Fi Alliance website states that Wi-Fi:
- Stands out as the most commonly used wireless technology.
- Serves as the primary medium for worldwide internet traffic.
- Has driven a staggering $3.3 trillion dollars in the global economic ecosystem.
- Has seen unprecedented growth, with more than 4 billion devices shipping every year and 16 billion devices in use.
Developed by the Wi-Fi Alliance, Wi-Fi, an acronym for Wireless Fidelity, is a wireless networking protocol based on the 802.11 IEEE (Institute of Electrical and Electronics Engineers) network standard. It has revolutionized the way people have communicated for over two decades. Using radio waves, Wi-Fi allows multiple devices to connect to the internet in a home setting or business environment through a wireless router, which in turn links directly to your internet modem and functions as a hub to broadcast the internet connectivity to all the WIFI-linked devices such as cell phones, tablets, and TVs, etc.
Wi-Fi allows relatively greater mobility within the network coverage, and the typical range varies from 125 feet to 250 feet.
As Wi-Fi is the most sought-after wireless technology today, it is imperative that the network and data security be of top-notch quality.
Through Wi-Fi Protected Access (WPA), the WI-FI Alliance has been at the forefront of ensuring secure digital communications for individuals and enterprises by using Authenticated encryption, HMAC (Hashed Message Authentication Mode) with Secure Hash Algorithm (HMAC-SHA256), and Robust management frame protection.
Cellular-based Long Range Protocols in IoT
The long-distance cellular communication protocol is mainly the standard and protocol adopted by various telecom operators under 2/3/4/5G, NB-IoT and other technologies. Here we are going to talk about LTE Cat 1 (alo LTE-M). Compared to other cellular connectivity solutions, LTE-M is low-powered and provides significant reductions in maintenance expenses. It also has the huge benefit of being backwards compatible with current LTE networks, saving carriers money by preventing the need to build a new station.
LTE-M
LTE-M stands for Long-Term Evolution for Machines, which is a low-power wide area network using radio frequency waves for M2M (Machine to Machine) and Internet of Things (IoT) applications. Backed and developed by 3GPP, LTE-M provides a perfect narrow-bandwidth mobile communication solution to enable IoT devices such as smart sensors, actuators, regulators, and industrial Cellular gateway devices to transmit data while ensuring relatively less power consumption and high signal penetration.
Read further: Cellular connectivity for IoT
LTE-M eclipses other IoT protocols in terms of providing reliable worldwide connectivity, which makes it the perfect choice for a live status update for fleet tracking, IoT remote monitoring, asset tracking, alarm panels, and POS (point-of-sale) devices. In low-coverage remote locations where the LTE signal strength is low, the system can easily downgrade to 3G (WCDMA-Wideband code division multiple access) or 2G (GPS-General Packet Radio Service) to ensure connectivity.
Using a cell-tower positioning system, LTE-M also provides cost-effective basic location tracking facilities to OEMs for their devices. A SIM, or Subscriber Identity Module chip, is embedded in the circuit board of every LTE-M device and the carrier keys are incorporated, which makes it one of the most secure IoT protocols out there as the keys cannot be altered without having physical access.
However, as a subscription to any of the cellular carriers is mandatory for SIMs to operate, the associated costs tend to be ongoing. The latest release, 14, offers a data rate extended up to 4Mbps, providing enhanced mobility and reliability for the network.
Non-Cellular Long-range IoT Protocols
ZigBee
The term “ZigBee” refers to the way bee colonies communicate, in which bees dance in zigzag patterns to relay information such as the direction, location, and distance of food sources. Zigbee is a new generation of wireless communication technology.
Read further: BLE vs Zigbee
Zigbee Features
Owned by the ZigBee Alliance, an alliance of multiple companies which have developed and published this standard, ZigBee was conceptualized in 1998, standardized in 2003, and then revised in 2006. As stated on their website, the ZigBee protocol is incorporated and deployed in millions of devices across the world.
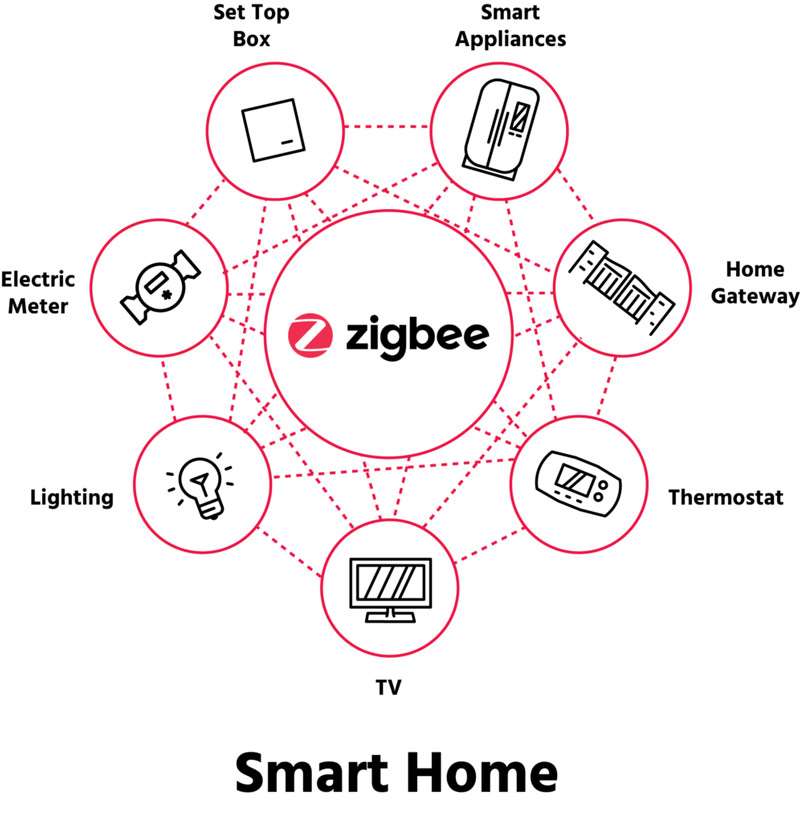
In the majority of countries around the world, Zigbee uses the industrial, scientific, and medical (ISM) radio channels and operates at a frequency of 2.4 GHz (Giga Hertz). In the majority of countries around the world, Zigbee uses the industrial, scientific, and medical (ISM) radio channels and operates at a frequency of 2.4 GHz (Giga Hertz). Transmission distances are limited by its low power consumption to 10-100 meters line-of-sight, depending on power output and environmental factors. Zigbee is best suited for sporadic data transmissions from a sensor or input device because it has a predetermined rate of up to 250 kbit/s. Zigbee networks are additionally protected by 128 bit symmetric encryption keys. As a result, ZigBee ensures a low-powered, low-bandwidth, close-proximity, wireless ad hoc network that is secure and easily scalable.
Zigbee Mesh
Zigbee provides mesh ad hoc networks and enables multiple wireless pathways for network nodes to connect to one another. By using such a mesh network of intermediary devices to relay data across long distances, Zigbee devices are able to reach farther-off devices. Zigbee mesh network can theoretically accommodate up to 65,000 Zigbee nodes.
Zigbee Uses
Zigbee is typically used in low data rate applications that require long battery life and secure networking. It enjoys advantages of low cost, high network capacity, security, and reliability. Also, ZigBee prolongs the power supply battery life of the IoT products to the greatest extent. Therefore, it is the perfect technical option for the transfer of data for various industrial field automation controls. Moreover, the technology defined by the Zigbee specification is meant to be less complex and less expensive than other wireless personal area networks, such as Bluetooth and Wi-Fi.
Read further: BLE vs WiFi
The smart home is also the most commonly seen use example of the ZigBee. This technology can connect multiple smart home devices together at the same time. As an ideal choice for the home network environment, users can realize the connection between devices such as smart door locks, lighting control, robots and thermostats, and add a universal Zigbee gateway to connect to the Internet and to perform real-time command control.
Zigbee can specifically be used for smart building and home automation, including IoT lighting control, air conditioning, curtains, and other home appliance; consumer electronics equipment, including remote control of TVs, DVD players, CD players, and other electrical devices; Automatic collection, analysis and processing of medical equipment as well as IoT remote management of medical sensors, patient emergency call buttons, etc.
Things need to know about Zigbee:
On its 15th anniversary, the ZigBee alliance launched “Dotdot”, which is an IoT basic language. Dotdot enables multiple smart devices to work coherently on the ZigBee network, Internet Protocol, and various others. Dotdot over thread technology has also been introduced, which is an IPV6 protocol allowing home device connectivity.
LoRaWAN
Just like ZigBee, LoRaWAN (Long Range Wide Area Network) is a proprietary technology developed by the LoRa Alliance, which is a non-profit organization. The LoRaWAN protocol is a set of transmission protocol standards based on the physical layer transmission of LoRa and mainly based on the data link layer. LoRaWAN corresponds to the MAC layer in the OSI seven-layer model. It is an open network protocol that eliminates the incompatibility of hardware, and also has features such as multi-channel access, frequency switching, adaptive rate, channel management, timing sending and receiving, node access authentication, data encryption, and roaming.
As the name suggests, LoRaWAN falls into the category of wide area networks. Hence, LoRaWAN is the preferred option for enterprises aiming to develop a wide area network for battery-powered IoT gadgets. LoRaWAN is widely used for monitoring control devices and sensors deployed in large areas such as cities or localities. Using unlicensed radio bands, it can perform city-wide streetlamp control, management of agricultural farm control systems, and other environmental sensors.
Fine-tuned for long-range communication, LoRaWAN deploys multiple sub-gigahertz frequency bands depending on the operational region. In North America, the 915 MHz band is used. 868 MHz for Europe, while the 169 and 433 MHz bands are also in use. The normal data rates vary from 0.3 kbps to 50 kbps.
Learn more about the LoRaWAN frequency details HERE:
Most Popular IoT Protocols List in Tabular Form
| Owner | Frequency (MHz) | Range | Power Requirement | Security | Compatibility | |
|---|---|---|---|---|---|---|
| ZigBee | ZigBee Alliance | 868-868.6 (EU) 902-928 (US) |
10-100 meters line-of-sight | Low power, Battery less | Low, Basic encryption | Compatible across ZigBee devices Dotdot OS |
| LoRaWAN |
LoRa Alliance | 169,433,868 (EU) 915 (US) |
Up to 6 miles or 10 kms | Low-power | Basic 64-128 bit encryption | Depends on OEM |
| LTE-M | GSMA-_Cellular carriers | LTE bands: 450-2350 (uplink) |
Global | Band Dependent | NSA AES-256 | Application dependent |
| Bluetooth | BSIG (Bluetooth Special Interest Group) | 2400 | 10-30 meters | Low Power typically 100mW | 128 bit encryption | Bluetooth devices |
| Z-Wave | Silicon Labs | 908 (US) 868 (EU) |
30-100 meters | ¬2.5mA | AES 128 | Z Wave devices |
| Wi-Fi | Wi-Fi Alliance | 2.4-6 GHz | 20-150 meters | 5-20 Watts | WPA-3 | Wi-Fi devices |
IoT Protocols Can Be Used In These IoT Hardware
IoT protocols need to be used on IoT hardware devices. Different IoT projects may require different IoT hardware with different functions, but the underlying developmental structure remains the same. We will discuss some of the key hardware an IoT project must have.
IoT Sensors
As the name suggests, an IoT sensor is a device that detects a change in the physical state of any system and converts it into an electrical signal which is then transmitted to the central processing hub.
Sensors have various types i.e. optical, pressure, contact, acoustic, humidity, magnetic, chemical, and many more depending upon the physical change required to be detected.
IoT Gateway
What is an IoT Gateway and Why is it Indispensable?
Working as a bridge, an IoT gateway essentially serves as a central connecting hub for the IoT devices and links them to the cloud and to one another facilitating communication, and manipulating raw data into useful information using any of the IoT protocols discussed earlier. An IoT gateway also functions like a computing platform having built-in customized applications to manage devices, and data, ensure security, and various other gateway functions.
For a more in-depth view of IoT Gateways, Check out this article for more info:
How to Choose Proper IoT Protocols for Your IoT Projects
It is difficult to determine which of the IoT protocols discussed above is the best for your IoT projects, but the winner is definitely the one that is easily available and at a suitable speed on most newly manufactured IoT devices and mobile phones. However, based on the current variety of use cases, the crux of the matter is not to find the “best” option, but to find the “best fit” option based on the needs.
In real-time, there will always be some sort of give-and-take scenarios where you might have to compromise on some factors. For example, a long operational range requires increased power consumption levels and hence an increased associated cost. Therefore, you need to chalk out your design criteria and then begin narrowing down your options till you find the most suitable one.
Wi-Fi would be ideal if you need to transfer large amounts of data and files over the network, while Bluetooth would be the first choice if you want to make retail proximity marketing.
In conclusion, a successful IoT protocol choice depends entirely on what you wish to achieve, and the key aspect of choosing perfect wireless IoT protocols for your IoT project is to pen down your requirements clearly so that you can focus only on viable options. These requirements can be the data transmission rate, operational range, power consumption, and the cost of the whole project.
Here are some key factors which you must consider while choosing the right wireless IoT protocol for your IoT project.
Data Volume to be Transmitted
If your project requires huge chunks of data to be transmitted, like high-resolution pictures or videos, or large sensor data files, you must choose an IoT protocol that can transmit this huge data in a short interval. WLAN and Bluetooth protocols can be a great choice in such a situation, but they will consume a large amount of energy in the process.
However, the majority of IoT projects with smart sensor modules need the wireless transmission of small amounts of data in short bursts. In such scenarios, you can easily switch to low-powered solutions like ZigBee or EnOcean, which are designed specifically for ultra-low-power devices.
The Number of Devices Transmitting Data at the Same Time
For a wireless IoT protocol, the available frequency band is shared between the network devices. If you have many devices using the same frequency band at a given location, the radio signals can get distorted due to interference, resulting in data transmission delays and data losses.
Certain frequency bands are more widely used than others, which makes systems using certain protocols more prone to interference. The 2.4 GHz band is a good example — it’s used for the wireless networking of computers, printers, and other IT equipment and is license-free all over the world, making it a popular choice. Bluetooth and WLAN both use this band, as do the majority of ZigBee devices.
There are some other protocols that fall into the sub-1GHz band category, which means that the radio waves used in these protocols for data transmission have frequencies less than 1 GHz. You are much more likely to have interference-free transmission using these bands as they are much less populated.
Power Consumption of IoT Projects
If the IoT sensors deployed in your IoT project are battery-powered, you need to know the replacement period for the batteries. Furthermore, you will also need to dispose of them properly and ensure that you always have replacements ready to roll. Those seeking a low-energy, the low-maintenance IoT solution should consider less-power-comsuming batteries that is photovoltaic-powered, or in simple terms, uses solar energy as a power source. What’s more, choosing a low-energy wireless IoT protocol can unencumber you from all these hassles. Zigbee and BLE(Bluetooth Low Energy) are good examples.
Compatibility with Other Wireless Protocols and Platforms
Since there is a plethora of different IoT device manufacturers and automation systems, they usually use different IoT protocols. For example, in some complex industrial IoT solutions or projects, a company requires a large number of IoT equipment, sensors, smart terminals and other hardware to finish production. However, the IoT protocols supported by different types of hardware are varied. What’s more, Different industrial production scenarios and processes result in large differences in the degree of automation, informatization, and intelligence. Therefore, it is so difficult to fully interconnect all devices of a single enterprise. The entire Internet of Things is so fragmented and standardization is still on the way. So it is necessary to decide whichever IoT protocol you choose for your IoT project be compatible with other platforms and wireless protocols, and use IoT gateways to make IoT protocol conversion.
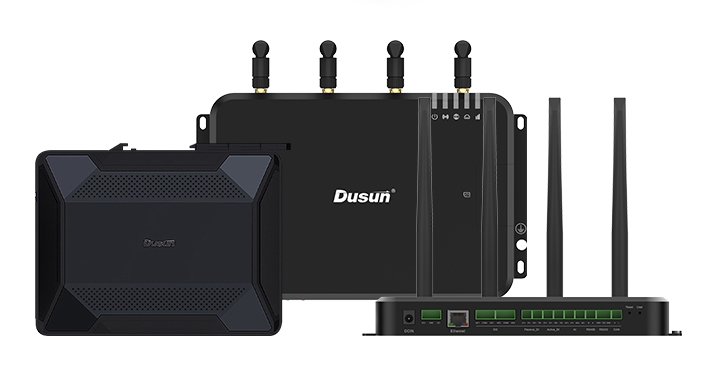
At Dusun IoT, we design IoT gateway hardware and IoT turnkey solutions that are compatible with LTE-M, Wi-Fi, BLE, Z-WAVE, Sub-G, LoRa, and many other IoT protocols. Our IoT gateways also support programming, secondary development, and other SDKs, allowing users to customize their IoT gateway applications easily.